Online Office Safety: 11 Work At Home Security Tips

Table of Contents
For the past few decades, as the digital revolution expands, more and more people are working from home than ever before. In fact, the percentage of American workers who did their jobs from home has been growing steadily since 2000, reaching an all-time high of 5 percent just last year.
However, as we know, the year 2020 has prompted rapid growth in the number of people working from home as the COVID-19 pandemic has forced millions to abandon their offices and turn their dining rooms or spare bedrooms into workspaces.
Yet even as some businesses start to open back up, including offices, many companies are electing to allow their workers to continue working from home at least through the rest of the year. This may still extend further even after the virus is successfully contained. Recent estimates indicate that around 20 percent of companies will make their pandemic work-from-home policies permanent, representing a significant change in how we work.
For many, this is welcome news. But working from home comes with some risks, as your home network tends to be less well protected against cyber criminals than a corporate one. Implementing the right defenses is essential to keeping yourself and your company safe, and below, you can find out everything you need to make sure your home office is fully secure.
Cyber Security Threats in 2020
Before going into the specific things you can be doing to maximize your home office’s security, we wanted to discuss the various threats that are out there so that you can better understand why these measures are necessary and what they do.
There are many different dangers out there, but the most prevalent include:
Hacking and Data Theft
Hacking just means that someone who does not have the authorization to access a system manages to get into it, which almost always leads to data theft. Hackers want things such as credit card numbers, bank information, login details, social security numbers, and anything else valuable they can get their hands on and then sell for a profit.
The typical line of thinking is that hackers tend to go after larger companies as that’s where the useful data is (and also because they can get more information with one hack, increasing their efficiency). But these large companies also tend to have the strongest defenses, making them the most difficult to hack.
As a result, small businesses are increasingly becoming the preferred target for hackers and other cybercriminals, mainly because their defenses tend to be weaker, yet they still hold valuable data. In fact, around 43 percent of all cyberattacks are aimed at small businesses. The logic is that it takes the same amount of effort to hack several small companies, and produces more results than trying and hack into a big company.
If you thought you were safe because you work for a small company, “no one would bother to hack," know that this is no longer the case, and you need to be taking cybersecurity as seriously as everyone else.
Identity Theft
Identity theft occurs when a cybercriminal assumes your identity and then does things on your behalf. In a worst-case scenario, they get a hold of your social security number and other personal details. They then use this information to withdraw money from your accounts, make charges to your credit and debit cards, and even open up new credit lines that could get you into real trouble with creditors.
If you’re working from home, identity theft becomes even more of a concern because if your identity is stolen, cybercriminals may be able to gain access to your company’s servers, compromising its data and potentially costing a lot of money.
Viruses, Malware, Ransomware, and Worms
While all slightly different, these are all programs that make their way onto your computer, usually because you click a bad link or open a dangerous spam email. They do various things to your computer. For example, ransomware will literally hold your device “hostage," shutting it down until you either hand over sensitive data or give money.
Malware is more common and can often go undetected. It slows down your computer, and at best is a nuisance that can get in the way of your productivity. At worst, it can take personal information off your device and send it to people who will use it to steal from either you or your company.
Cyberbullying
Not typically thought of as a cyber threat, cyberbullying is quite prevalent in our society, and, contrary to popular belief, it’s not just something that kids do. A study by Pew found that around 40 percent of adults have experienced some sort of online harassment, and 75 percent of adults have reported seeing it taking place around them.
If you’re new to working online, it’s essential to be aware of how you’re interacting with others. Comments or jokes that might have gone unnoticed, or were better contextualized, when spoken in the office, can seem aggressive or harmful when typed out in a message.
Being aware of this is vital to protect yourself (cyberbullying is a crime, and even if you’re not convicted in a court of law, it can lead to termination) and those you work with. Both are important aspects of keeping your company moving forward.
The Reality of the Threats We Face
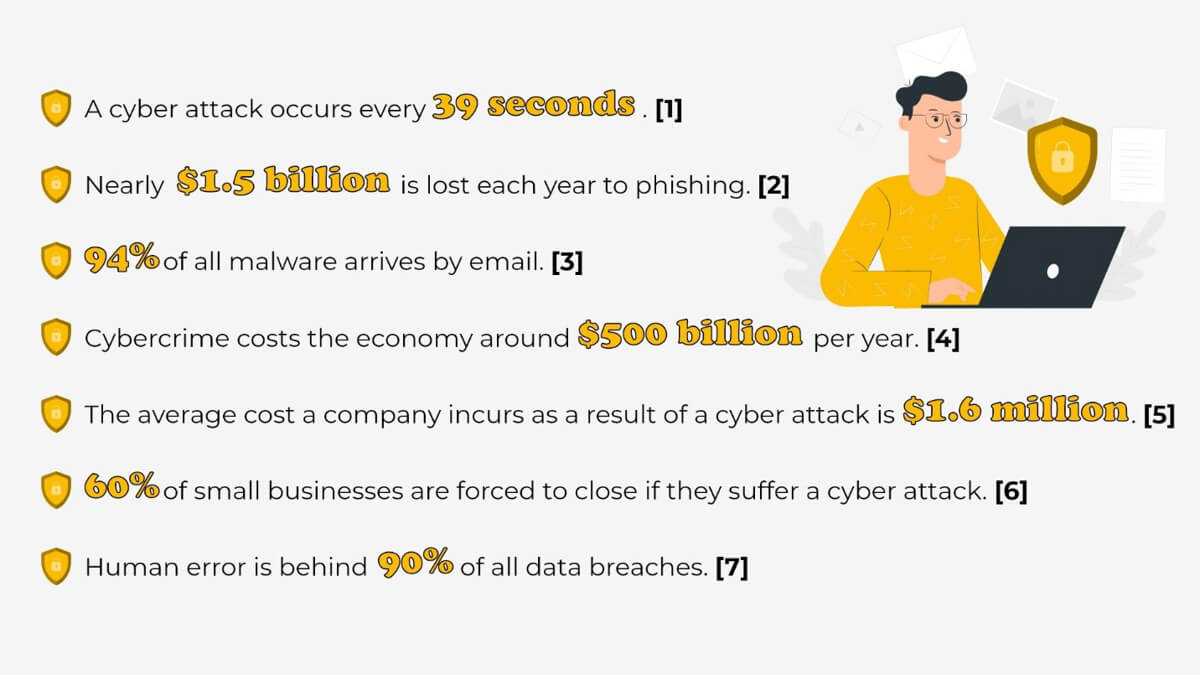
Now that you have an idea of the threats that are out there, here are some numbers that should help drive home just how serious this issue is and why it requires so much of your attention.
[/et_pb_text]
[1], [2], [3], [4], [5], [6], [7]
Whether you’re new to working online from home due to the pandemic, have been at it for a while, or plan to continue to do it moving forward, all of these numbers should be concerning. However, the last four are particularly troublesome. They point to the massive expense a cyber mistake can force your company to incur, and they also indicate that you, as an employee, are the one most likely to be responsible for such a mistake.
Don’t let this strike fear into your heart. If you take the proper steps to protect yourself in your new home, then you can be sure that you won’t be the one who brings on this data breach that could have catastrophic consequences for not only yourself but also your employer.
11 Work at Home Security Tips
Now that you are aware of the threats that you face when working from home, as well as their prevalence and potentially catastrophic consequences, it’s time to look at what you can do to make sure your home office is secure.
1. Review Company “Work From Home" Policy
When you begin to work from home, the very first thing you should do is review the company’s existing “work from home" policy. This should include all the information the experts have deemed necessary for you to know about the dangers you might face, and there should also be plenty of information about best practices you can use to make sure you’re safe.
These policies will typically provide instructions about passwords, data sharing, access, authentication, and more. If you read through it and come across things that aren’t entirely clear, then make sure to speak up and ask for clarification; your entire company’s cybersecurity might be resting on it.
A copy of this policy should be given to you once it has been established that you’ll be working remotely. If it’s not, ask for it. If it doesn’t exist, then you should speak with your manager about making one since a document like this is often essential to making sure employees are educated and informed about what they need to be doing.
2. Make Sure Everything is Password Protected
Although they seem simple, passwords are a huge component of cybersecurity. They act as the first line of defense against potential hacks or other unwanted access attempts, and not using passwords is equivalent to leaving the front door of your house unlocked. Ignoring them means cybercriminals will be able to get past your first safeguard without much issue, significantly increasing the chances of a full-on hack and data breach.
When we say password protect everything, we mean everything. This means your computer, laptop, smartphone, and all of your accounts. Make sure you’re mixing up the passwords you’re using, i.e., you’re not using the same one for multiple accounts, and that you are practicing good password habits, which include:
- Overall, setting passwords and following good habits is easy to do, but it is one of the most significant defenses you can use against hackers and other cybercriminals.
3. Lock Computers Not in Use
One good habit to adopt is to make sure that you’re locking your computers when you’re not using them, especially those you’re using for work. This means either turning them off or using the lock feature found by pressing “CTL + ALT + Delete."
For those who have lots of experience working in an office, this is probably not something new, but it’s reasonable to think you don’t need to do this when you’re at home. Getting into this habit will ensure that you never leave your devices vulnerable to attacks from hackers and other cybercriminals.
4. Improve the Physical Security of Your Home Office
Now that you’ve moved into a home office, you need to accept that there might be additional threats you didn’t face before, such as a break-in. Of course, we all don’t want to think this is possible, but there is no limit to what cybercriminals will do if they’re chasing after what they perceive to be valuable information.
As a result, you will want to take some steps to ensure the security of your office. This includes making sure there is a working lock on the door, installing locks on desk drawers and filing cabinets, and making sure computer screens are not visible from the outside.
Of course, if you live in a secluded area where there’s no chance someone sees inside your home, this last step might not be entirely necessary. Still, those living in bigger cities where there are more prying eyes would do well to ensure they’re working in privacy while in their home office.
5. Enable Two-Factor Authentication
Two-factor authentication is a security feature offered by lots of companies and organizations providing online services. All it means is that you need to go through two identity verification stages to gain access to your account. Usually, this means entering your username and password and then providing a code that is sent to your phone or email (which you have provided) to confirm you are indeed the person you claim to be.
This is particularly effective because while hackers might be able to get past your password if they are really savvy, it’s almost impossible for them to guess this second part, making it that much more difficult for them to get access to your account. It’s also a great way to detect when your account is under attack; if you get a code sent to your phone when you haven’t tried to access that account, you know something is up and can take swift and effective action.
However, while many places are now offering this service, it is often not put into action until you yourself activate it, so you will need to seek it out and actively set it up, which we cannot recommend more that you do.
6. Train Yourself to Detect Phishing
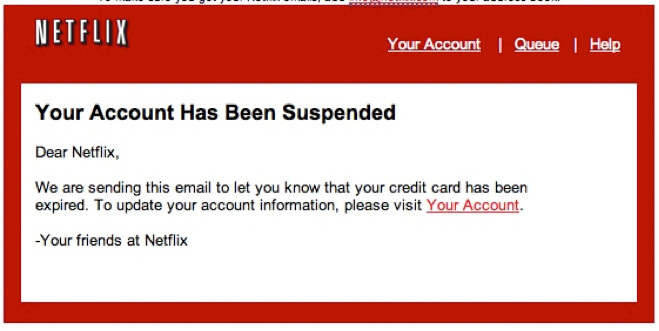
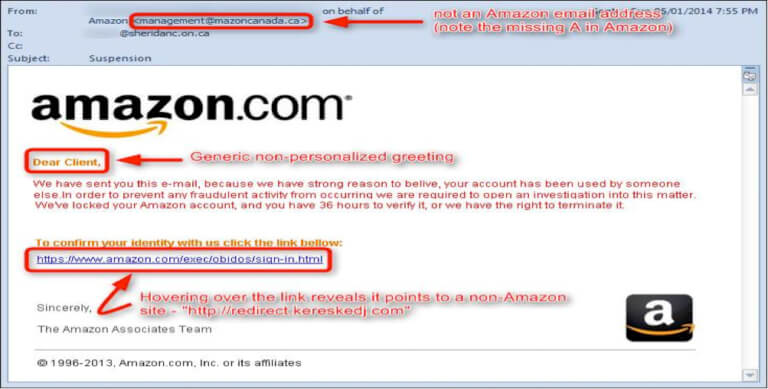
As we’ve already mentioned a few times, phishing is one of the main ways hackers and cybercriminals do their dirty work. For those who don’t know, phishing is when hackers use emails or other disguised messages to look legitimate so that you will willingly hand over sensitive information. Other forms of phishing, such as spear phishing, target specific individuals and are often much more personalized, making them more effective.
Some good examples of phishing attacks can be found below. One is made to look like a message from Netflix, and another is designed to look like something from Amazon. They show just how good hackers can be at what they do and why they can dupe so many people into handing information over that they should be safeguarding.
- As a result, you need to learn how to be extra vigilant so you can spot phishing attempts and keep yourself safe. Some things you can do to spot phishing include:
- Double check the sender address in an email. Fake emails will often come from somewhere different and not from where communications from that company typically originate.
- Hover over links you’ve been asked to click on to see if they really lead where they say they do.
- Look for spelling mistakes or other errors; hackers are notoriously lazy.
- Do a quick Google search to see if the claim being made in the email is real. If it’s not, there’s a good chance that the company in question will have issued a statement.
- Familiarize yourself with the different policies being used by the services with which you have accounts. Some say they would never ask for credit card information in an email, so if that’s happening, you know it’s fake.
Learning how to spot phishing is a bit of an art, and it takes practice. Luckily, to help you, Google has put together this tool to help teach you to spot phishing. Play around with it so that the next time a suspicious email comes through, you can spot it.
We should note that your email client’s spam filter should catch a lot of this, but plenty of stuff still sneaks through. Don’t think that having spam filters activated is going to completely protect you from the many different threats out there.
7. Use Anti-Virus Software
Anti-virus software is pretty much a no-brainer when it comes to keeping your home office secure. It will identify threats as they come up, guide you to safe websites by alerting you when you’re visiting one that isn’t secure and help you remove milder versions of malware while minimizing the damage they can do.
For PC users, the need for anti-virus software is even greater, but this doesn’t mean Macs are entirely safe. In this case, it’s probably best to speak with someone at your company. They may have a preferred software they want you to use, and if this is the case, they should be able to provide it for free or at the very least at a discounted rate.
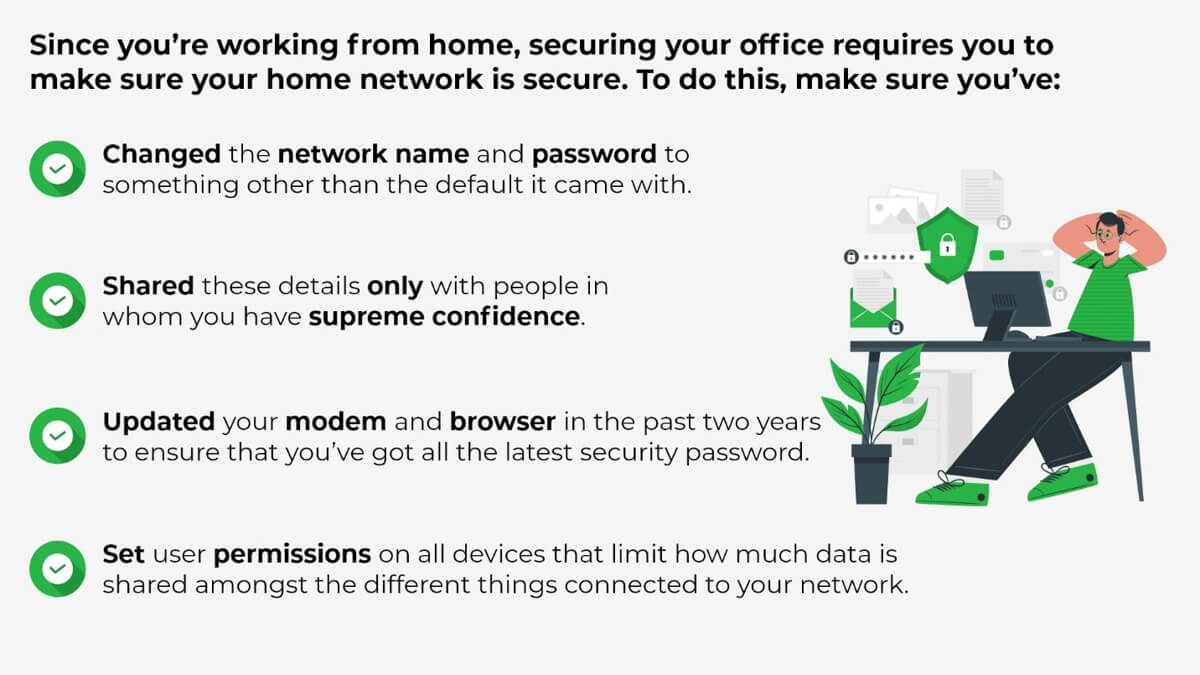
8. Ensure Your WiFi is Protected
The security of your home WiFi network is a key part of your overall home office security strategy.
9. Download a VPN
One thing you may want to consider is installing and using a virtual private network (VPN). These programs encrypt your WiFi connection, which puts up another layer of security and also hides your online activity, helping to improve privacy and keep hackers away.
Depending on the size of the company for which you work, doing this may be a requirement to be able to work from home. But even if it’s not, it still might be something to consider as it will make your network that much more secure.
One thing to note is that using a VPN will likely slow down network performance, so you might not want to use it constantly, or you may want to look into upgrading your connection so that using this security feature won’t slow things down.
10. Ask About Data Encryption
Encrypting data on your computer means that it can only be accessed by those who possess the key that unlocks the encryption. It’s typically used as a safeguard in the event a device is stolen; the person who has it would be unable to access the information stored on the device.
For those using a company device, there’s a good chance this is already installed and activated, but you may want to ask if there is anything you need to do to make sure it’s appropriately set up. If you’re using your own device, there’s a good chance it does not have this feature, so you may want to find out if this is something you should set up to make sure you’re fully protected from any possible threat.
11. Back Up Files Regularly
Losing files is frustrating and can be dangerous if they happen to fall into the wrong hands. If your computer does come down with a virus, sometimes the only thing you can do is wipe the hard drive and start again. All of this means that if you haven’t backed up your files, this can be catastrophic.
So, set up a system to make sure everything is regularly saved somewhere else. You can either do this manually using an external hard drive or by using a cloud service. If you do it manually, set up a reminder on your calendar to remember to do it frequently. Should you choose to use a cloud service, you can usually automate this, but maybe speak with someone at your company to ensure you’re using a service that meets their security standards.
Enjoy the Security of Your Home Office
Working from home provides tremendous benefits to those who have the opportunity to do it. However, as we’ve established here, it can also expose you and your company to a wide range of threats. But this shouldn’t be used as an excuse not to take advantage of the many perks of remote work. Just implement the security strategies discussed here, educate yourself about newly emerging threats, and remain vigilant at all times.

 Call now to find your best offers!
Call now to find your best offers!